Continuous Threat Exposure Management — Managed Picus Security Validation
CTEM is MakkariSecurity’s fully managed, collaborative programme for continuously identifying, validating, and reducing cyber exposure. We operate the cycle on your behalf, working shoulder‑to‑shoulder with your teams to deliver measurable risk reduction without the overhead of building an internal BAS/SCV/CTEM function.
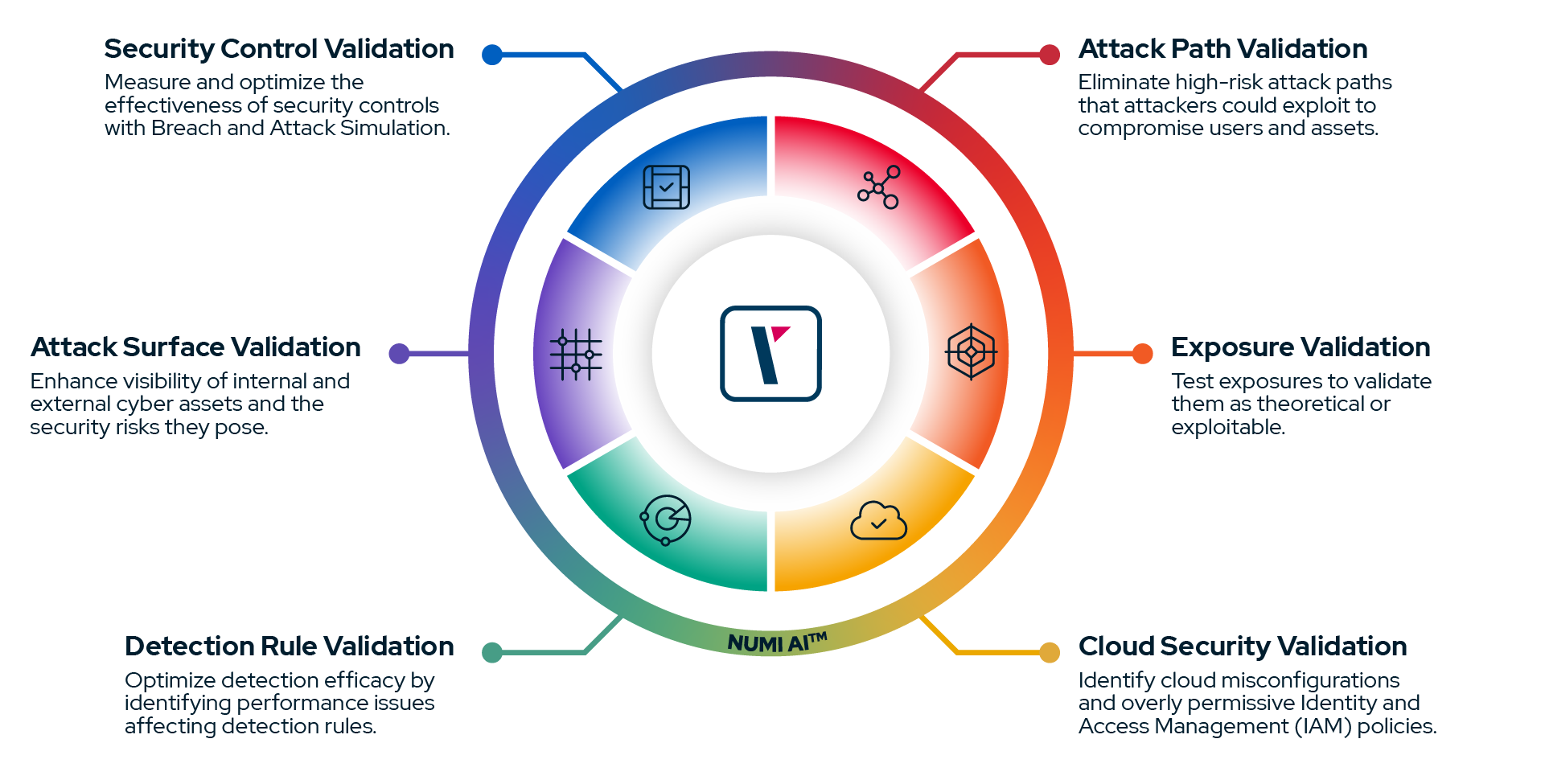
How our CTEM service works
- 1) Scoping together: joint workshops to define critical assets, processes and risk appetite; we agree success measures so the programme aligns to your priorities from day one.
- 2) Continuous discovery: MakkariSecurity continuously maps your attack surface and tracks exposures as they emerge across networks, endpoints, cloud and applications.
- 3) Risk‑based prioritisation: findings are ranked by exploitability and business impact; you receive a clear action list that focuses effort where it counts most.
- 4) Collaborative validation: in safe, controlled exercises we emulate real‑world adversaries and integrate results with your SIEM/XDR/SOC to confirm what’s effective and what needs uplift.
- 5) Mobilisation & remediation support: we recommend vendor‑specific rule changes, provide CAB‑ready evidence, implement changes with you, and replay scenarios to verify the gap is closed.
- CTEM alignment: we operate the validation core of your CTEM cycle — scope, discover, validate, prioritise and measure exposure reduction — and keep the loop turning.
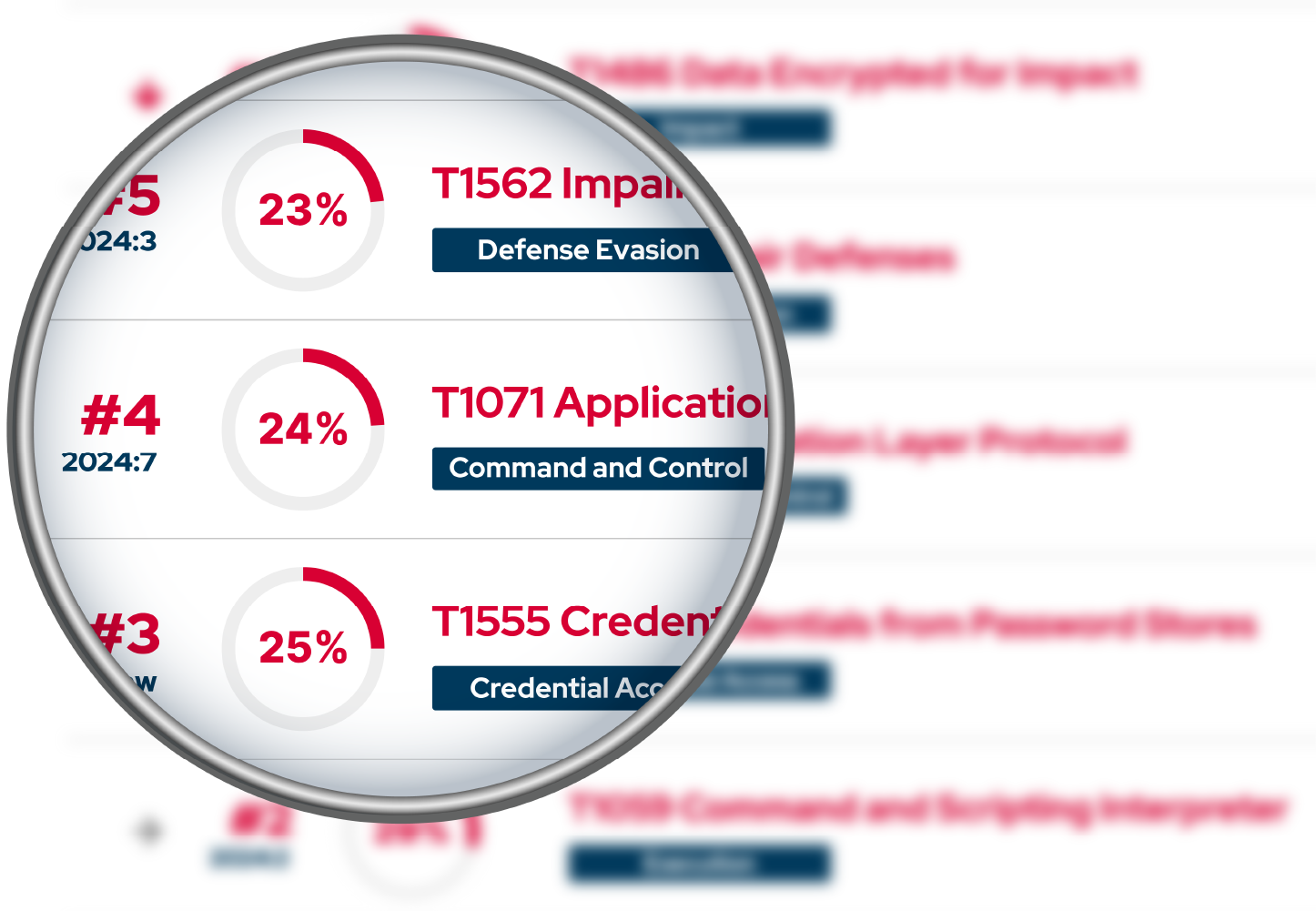
MITRE ATT&CK® heatmap / coverage visual.
Why a managed, collaborative model
- Time to value: proven playbooks, integrations and remediation templates get you results quickly; no need to spin up an in‑house CTEM function.
- Content freshness: leveraging the Picus Threat Library’s daily updates, our analysts select high‑relevance scenarios and suppress noise to protect SOC capacity.
- Actionable outcomes: beyond scores, we deliver concrete changes — detections, mitigations and control tuning that reduce MTTD/MTTM.
- Independent assurance: objective, repeatable testing and quarter‑on‑quarter metrics your board can trust.
- Lower total cost: avoid specialist hiring and platform maintenance while achieving continuous validation instead of annual spikes.
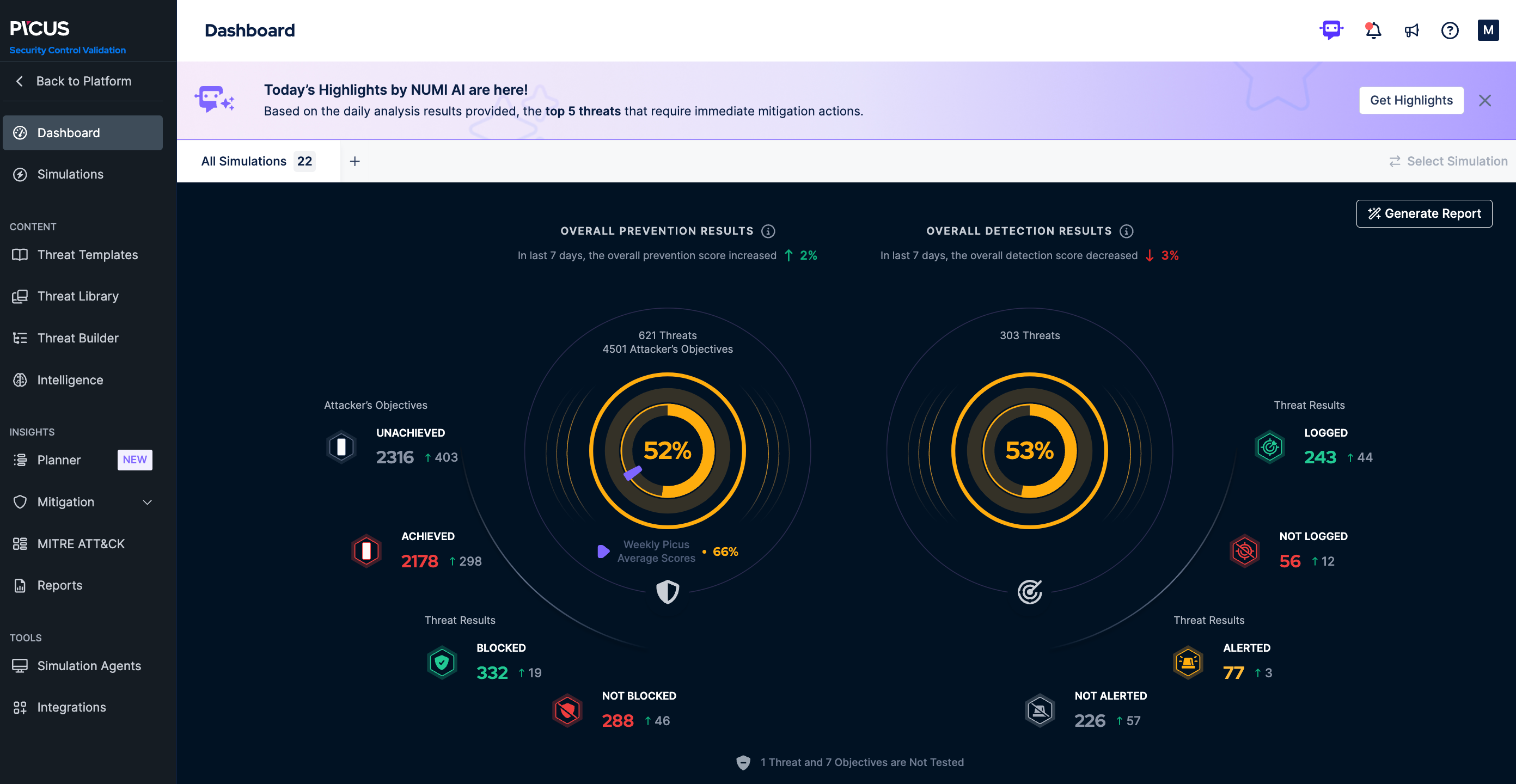
Outcome metrics we track with you
- Attack chain success rate ↓
- Mean Time to Detect (MTTD) ↓
- Mean Time to Mitigate (MTTM) ↓
- Critical gap closure rate ↑
- ATT&CK® tactic coverage ↑
Year‑round partnership
Managed wrap‑around: we run an agreed annual campaign programme on the Picus platform with quarterly reporting and actionable recommendations. We curate content, execute simulations, integrate and tune your controls, and translate findings into vendor‑specific change.
- Month 0–1: Onboard & baselines — enable the platform; connect SIEM, EDR/XDR, gateways and cloud; enable SCV/DRV/APV; establish an ATT&CK® baseline; set KPIs.
- Months 2–11: Operate & uplift — monthly targeted control checks across prevention and detection; curated threats; detection rule validation; mitigation PRs/CRs with rollback; purple‑team clinics and tuning.
- Quarterly: Scenario sprints — end‑to‑end adversary emulations (APV) with focus on frequent blind spots; executive reporting and roadmap updates; replay after change to verify fixes.
- Month 12: Evidence pack — board‑ready exposure‑reduction report: ATT&CK® coverage delta, prevention/detection trendlines, remediation completed, benchmark position and next‑year plan.
Deliverables each quarter
- Pre‑agreed campaign report with clear actions
- ATT&CK® coverage delta & heatmap
- Prevention & detection scores (incl. log→alert gap) + KPI trendlines
- Gap list with vendor‑specific fixes & CAB‑ready change tickets
- Detection content PRs (SIEM/EDR) with test evidence
- Scenario replay to verify efficacy post‑change
- Executive summary + ROI snapshot
- Optional board/audit evidence pack
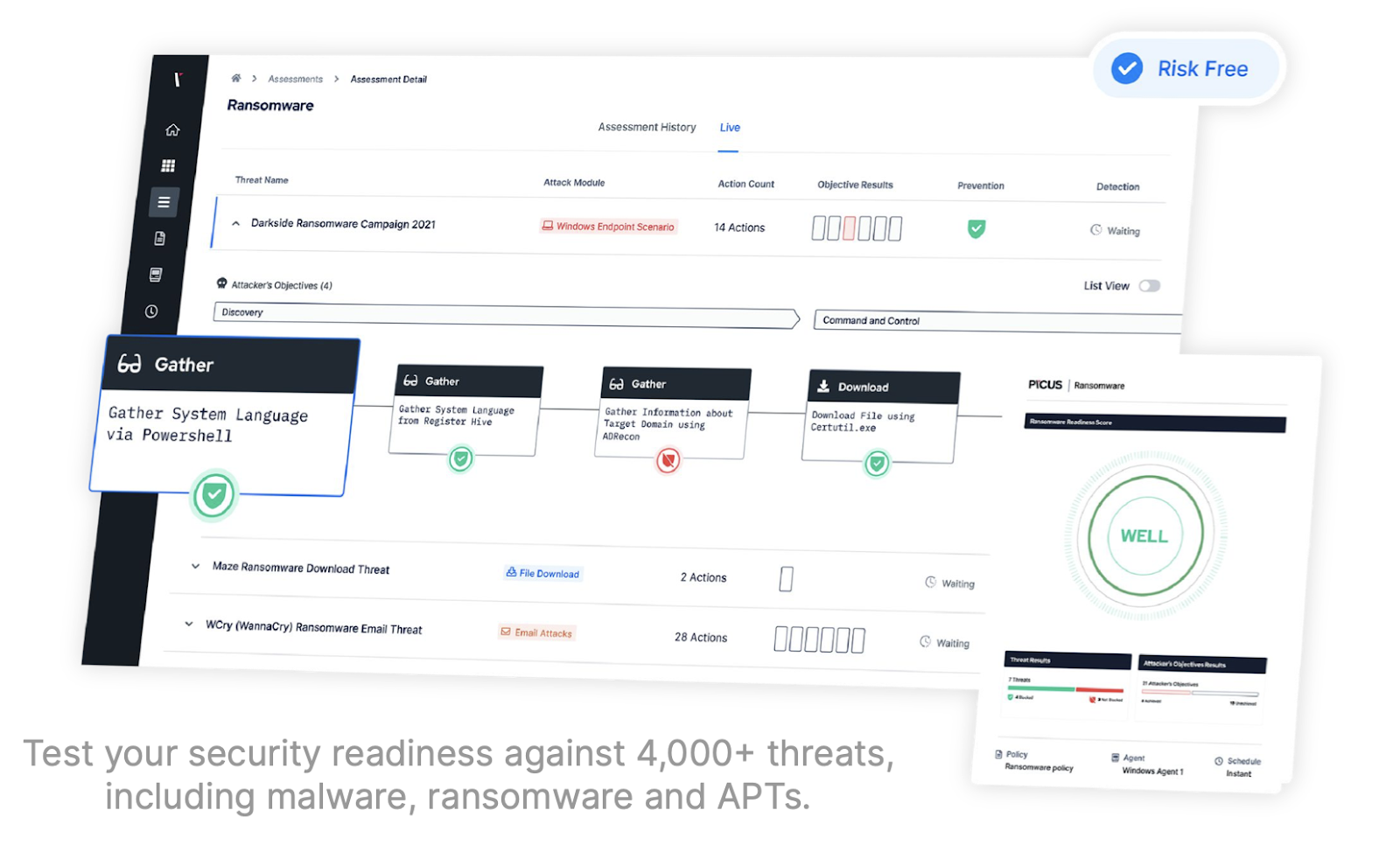
Integration diagram (Picus ⇄ SIEM/EDR/XDR ⇄ SOAR/ticketing).
- Platform capabilities: prevention and detection validation, ATT&CK® mapping, continuously updated threat library.
- Supported stacks: SIEM, EDR/XDR, firewalls, email/web gateways and major cloud providers.
- Change governance support: evidence suitable for CAB decisions with rollback considerations.
- Operational enablement: runbooks and dashboards aligned to your SOC and reporting cadence.
- Independent assurance: objective testing and benchmarking to complement in‑house teams.
Reporting & Governance
Our managed service embeds Picus into your governance model. On a regular cadence we provide concise summaries of outcomes, recommended actions, and trend views across prevention/detection performance and ATT&CK® coverage — giving stakeholders clear, defensible evidence without the maintenance burden of running the platform internally.

 Makkari
Makkari