Continuous Threat Exposure Management (CTEM)
Our managed CTEM programme (powered by Picus Security Validation) continuously identifies, validates, and reduces cyber exposure across on‑prem, cloud and hybrid estates. We run the full cycle with you and evidence measurable risk reduction.
What we solve
- Hidden assets and blind spots leave unknown risk exposure across hybrid estates.
- Point‑in‑time testing creates long windows of undetected risk between assessments.
- Difficult to track posture change and prove risk reduction to senior stakeholders.
- Designing relevant campaigns and keeping scenarios current is time‑consuming.
- Remediation is often prioritised poorly; low‑impact fixes consume limited capacity.
- SOCs drown in noisy alerts; true attacks slip through without continuous validation.
With CTEM you can…
- Validate prevention and detection continuously (not just annually).
- Benchmark ATT&CK® coverage and close drift with evidence‑based change.
- Prioritise by exploitability and business impact, shrinking the backlog.
- Report real‑world outcomes and trendlines your board understands.
Why Makkari
- Senior‑led delivery by practitioners who have handled thousands of breaches and built UK/EU‑wide practices.
- Blends DFIR, detection engineering and purple‑team expertise into one operating model.
- Aligned to NCSC / CREST / NIST good practice with board‑ready evidence packs.
- Transparent, collaborative approach — we work shoulder‑to‑shoulder with your teams.
- Rapid time‑to‑value via curated content, integrations and vendor‑specific remediation.
- Measurable risk reduction — tracked quarterly and replayed after change.
MAKKARI CTEM Core
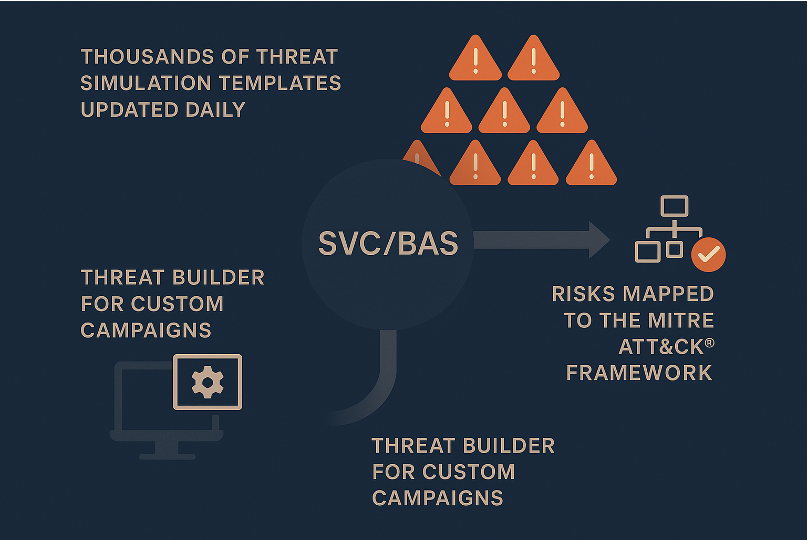
Security Control Validation (SCV / BAS)
- Simulates thousands of real-world threats (malware, ransomware, APTs) across SIEM, EDR, firewalls, gateways, and more.
- Validates both prevention and detection controls, mapping results to MITRE ATT&CK® to highlight coverage gaps.
- Tracks posture change over time to spot configuration drift and demonstrate measurable improvement.
- Provides vendor-specific remediation and rollback-safe change guidance with instant re-tests.
- Helps you prove ROI on security investments by showing exactly what is blocked, detected, or missed.
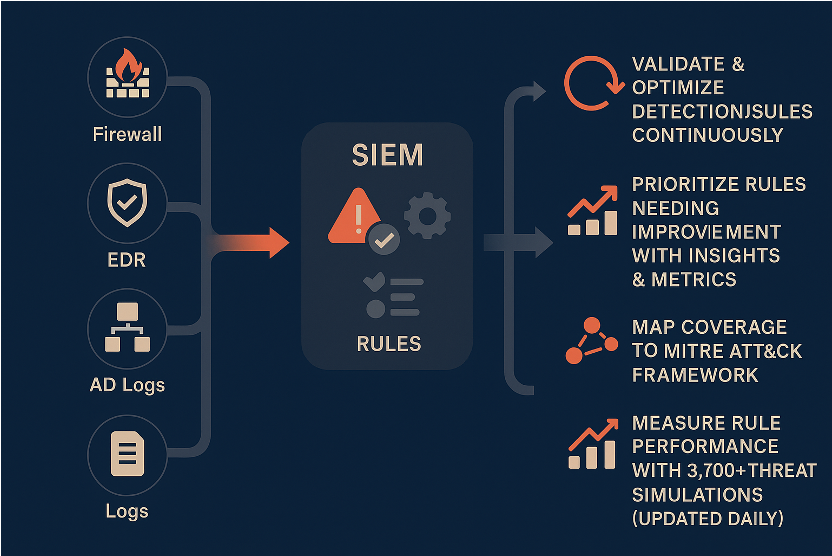
Detection Rule Validation (DRV)
- Continuously validates SIEM/EDR rules with safe, real-world scenarios mapped to MITRE ATT&CK®.
- Surfaces redundant, obsolete, and missing rules and measures coverage and alert frequency.
- Finds log-to-alert gaps before attackers do, optimising SIEM licensing and pipeline efficiency.
- Reduces tuning time from hours to minutes, freeing SOC resources for true incidents.
- Delivers performance metrics (FPR/FNR) and evidence for SOC and board reporting.
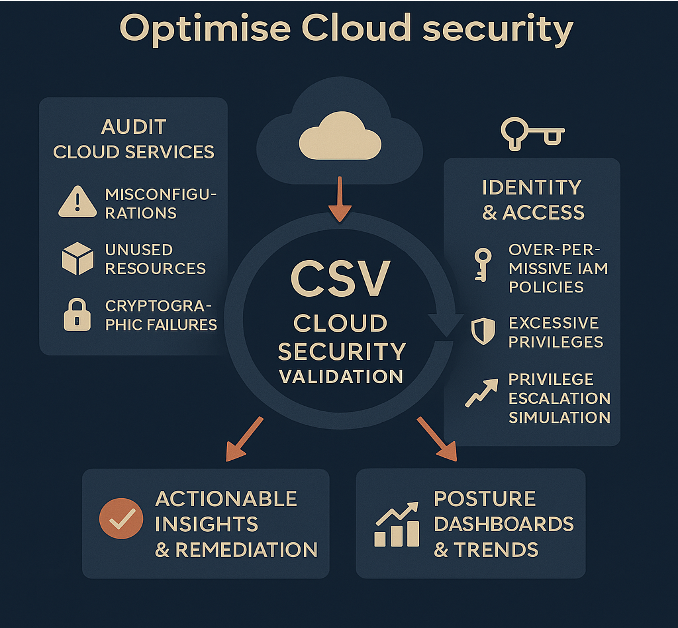
Cloud Security Validation (CSV)
- Audits AWS, Azure & GCP for misconfigurations, unused resources, and cryptographic issues.
- Identifies excessive privileges and runs privilege-escalation simulations to uncover real risk.
- Delivers prioritised remediation guidance to improve IAM posture and harden cloud security.
- Provides posture dashboards to measure and demonstrate improvement over time.
- Helps prepare for compliance and audit by proving security controls are working continuously.
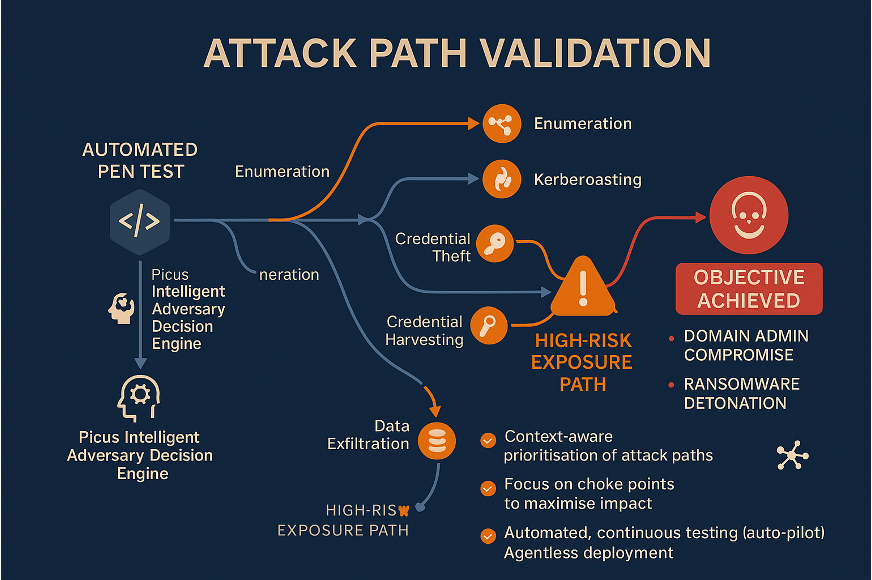
Attack Path Validation (APV)
- Combines automated pentesting with attack-path mapping to reveal full kill-chains.
- Shows how attackers could chain multiple small exposures to reach critical assets.
- Pinpoints “choke points” where one fix collapses multiple attack paths at once.
- Emulates techniques such as credential harvesting, Kerberoasting, and data exfiltration.
- Runs continuously to keep ransomware and domain-takeover risk minimised.
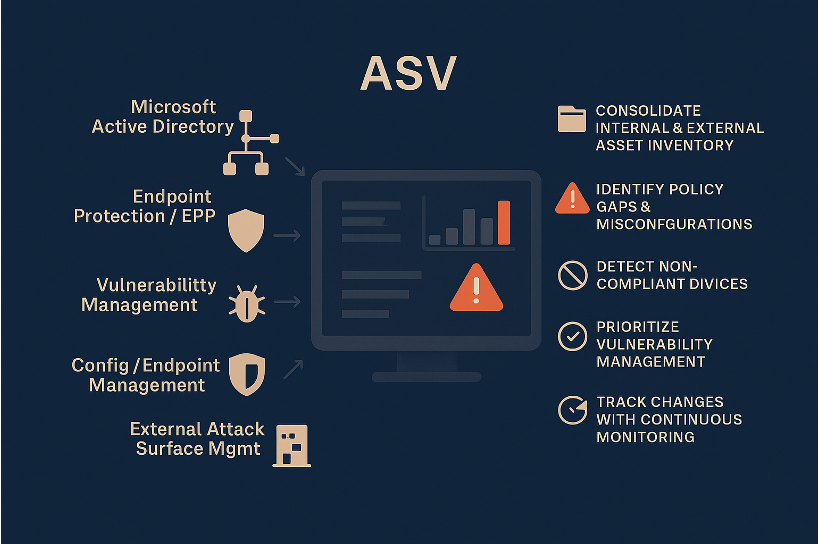
Attack Surface Validation (ASV)
- Aggregates and normalises data from AD, EPP, VM tools and external ASM platforms.
- Provides a single, live view of all internal and external assets.
- Highlights policy gaps, misconfigurations and non-compliant devices.
- Tracks changes in near real-time so shadow IT and rogue devices can’t go unnoticed.
- Prioritises vulnerabilities by asset criticality and business impact, helping CAB prioritisation.
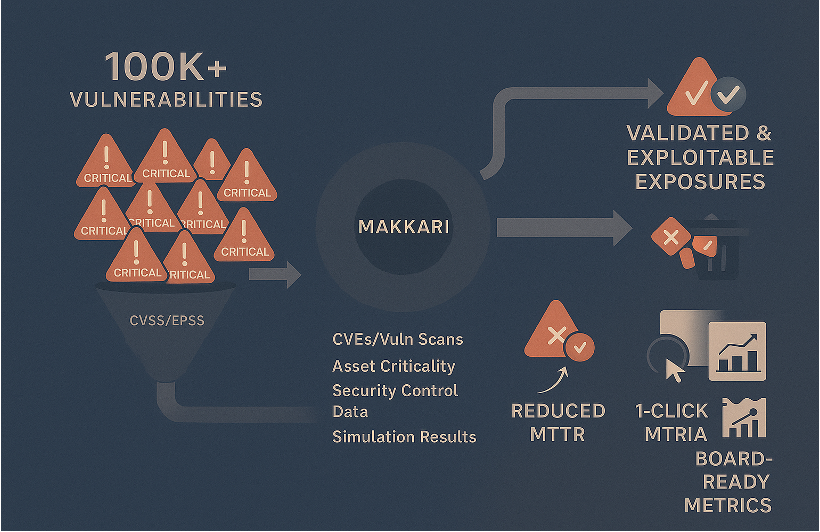
Exposure Validation (EVX)
- Runs continuous, safe exploitation tests to confirm which exposures are truly exploitable.
- Uses evidence-based scoring that blends CVSS/EPSS with live control performance.
- Automatically removes exposures already mitigated by existing controls.
- Produces clear, prioritised remediation lists to cut mean-time-to-remediate (MTTR).
- Outputs board-ready metrics that prove measurable risk reduction over time.
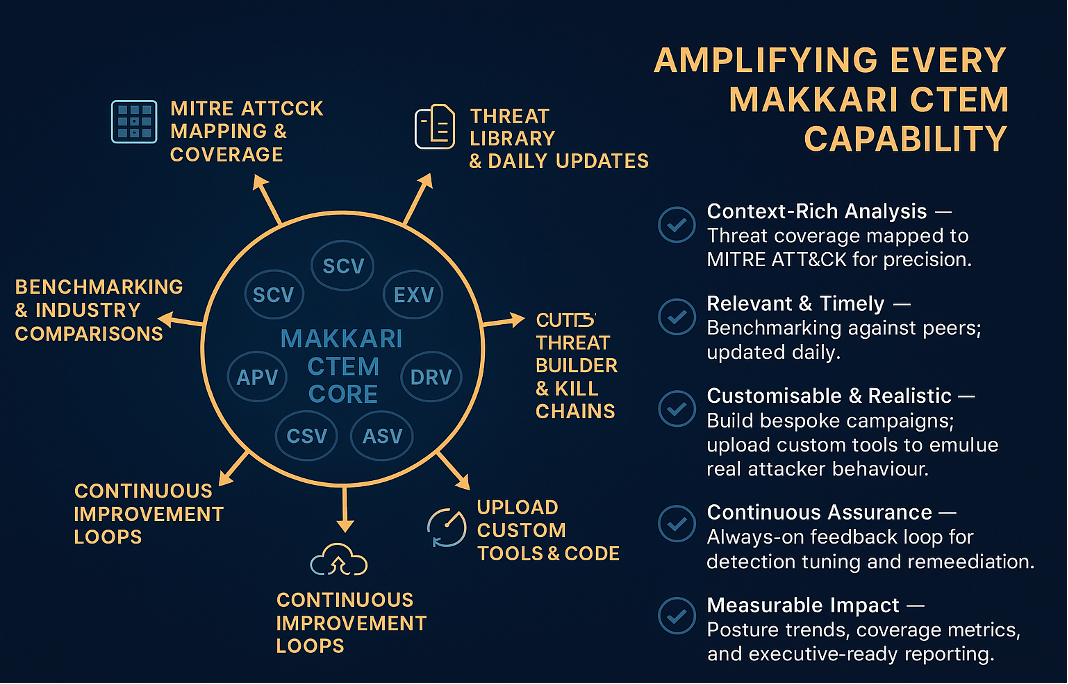
Bolstered services amplifying every capability
- Unified intelligence: benchmarking, MITRE ATT&CK® mapping, and curated threat intel feed each module.
- Adaptive & relevant: daily content updates ensure coverage stays current with attacker TTPs.
- Customisable campaigns: build targeted scenarios with bespoke payloads for your tech stack.
- Governance ready: CAB-ready change evidence, rollback guidance, and audit-friendly reporting.
- Outcome focused: continuous improvement loops with KPI trendlines and executive summaries.
How we operate
Monthly campaign planning
- Threat‑driven scenarios aligned to sector risks and latest intelligence.
- Runs around maintenance windows and blue‑team capacity.
- Ongoing attack‑surface review includes newly discovered assets.
Onboarding & enablement
- Kick‑off workshops and objective/KPI alignment.
- Environment setup & integrations (SIEM, EDR/XDR, Cloud, ASM).
- Tailored libraries and knowledge transfer.
Quarterly deliverables
- Campaign report with clear actions and KPI trendlines.
- ATT&CK® coverage deltas & heatmaps.
- Prevention & detection scores + log→alert gap analysis.
- Prioritised gap list with vendor‑specific fixes and CAB‑ready tickets.
- Detection content PRs (SIEM/EDR) with replay evidence.
- Executive summary and optional board/audit pack.
 Makkari
Makkari